
Successfully Defending Against Cyber Attacks

In the dynamic world of cybersecurity, companies must be able to respond effectively to security incidents. This capability is ensured through a combination of technologies and processes, primarily managed by a Security Operations Center (SOC), Security Information and Event Management (SIEM) systems, and Computer Emergency Response Teams (CERT). Together, they form the cyber defense center and thus constitute an essential part of any well-structured IT security line organization.
Dr. David Bauder, Thomas Kurz, and Dr. Carsten Woltmann on "Successfully Defending Against Cyber Attacks."
A key element in preparing and testing the readiness of the defense center is war-gaming. It serves to simulate potential security incidents and optimize the response to them. In doing so, weaknesses within teams and organizational structures are ruthlessly exposed and can be gradually addressed.
In this article, we explore the various components and how their interaction contributes to improving a company’s security strategy.
Incident Response Process: The Structural Foundation of Effective Cyber Defense
Security incidents can occur in various forms: phishing, familiar from the private sector, as well as attempted password cracking or malware infections, are probably the most common examples—often with severe consequences such as ransomware encryption attacks. However, security incidents can take much more diverse forms. Insider threats, where internal personnel misuse their access rights, can also cause significant damage. From our project experience, so-called "Advanced Persistent Threats" (APTs) are particularly noteworthy; these describe carefully planned, long-lasting, and targeted cyberattacks that remain undetected for extended periods.
Given the variety of threats, a structured approach to handling security incidents is essential. This is where the incident response process comes into play, consisting of four central phases:
1. Preparation: Establishment of security measures, processes, and training to respond quickly and effectively to potential incidents. This also includes regular exercises such as war-gaming to test and improve responsiveness.
2. Detection and Analysis: Identification of security incidents through monitoring systems such as SIEM or user reports. A rapid and accurate analysis is crucial to assess the severity of the incident and initiate appropriate measures.
3. Containment and Eradication: Immediate actions to contain the threat in order to minimize damage, followed by the complete elimination of the cause from the system. The measures and escalation levels are guided by the severity of the incident: severe events require comprehensive actions, involvement of company leadership, and, if necessary, notification of regulators, while less severe incidents follow a more moderate course of action.
4. Recovery and Follow-up: Restoration of affected systems and return to normal operations. This is followed by an evaluation of the incident (lessons learned) to gain insights and improve future security measures. Due to the evolving and constantly changing threat landscape, the incident response process itself is often further developed and improved during this phase.
SOC, SIEM, and CERT: The Interaction in the Incident Response Process
The Security Operations Center (SOC) is involved in all phases of the incident response process. In phase 1, it develops security policies, trains personnel, and provides the necessary technologies. During phase 2, the SOC continuously monitors networks and systems to detect threats early. In the event of an incident (phases 3 and 4), it coordinates the necessary response measures together with the CERT.
Security Information and Event Management (SIEM) systems are essential for the effectiveness of the process. In phase 1, they are configured to efficiently collect and analyze data from various sources within the IT infrastructure. They provide a centralized view of the security situation and support the automation and prioritization of incidents. During phase 2, SIEM systems identify suspicious activities and anomalies through continuous data analysis to enable a rapid response in the event of an incident.
The Computer Emergency Response Team (CERT) also plays a crucial role in the incident response process. In phase 1, it develops response plans, conducts training, and participates in war-gaming exercises to enhance readiness. In phase 3, CERT is responsible for the containment and eradication of threats, while in phase 4, it oversees system recovery and improves future security measures through follow-up analysis.
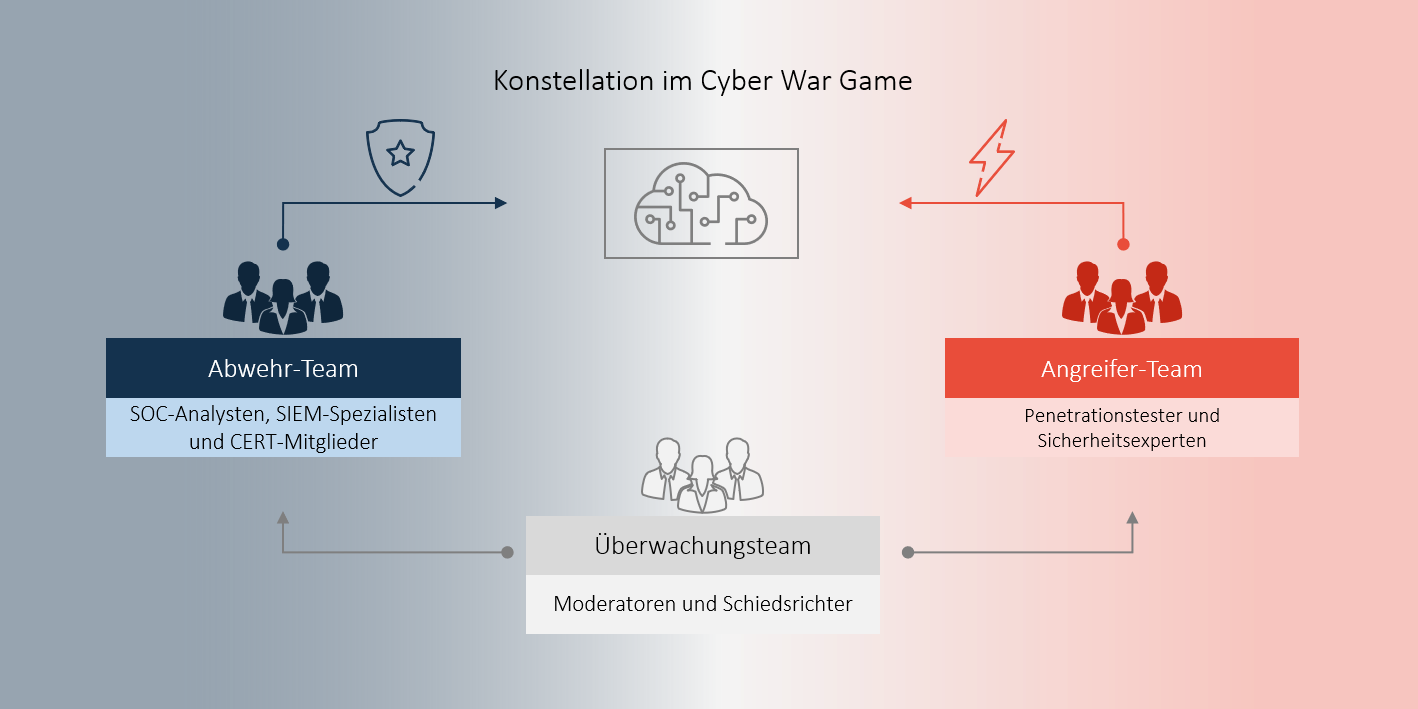
War-Gaming is a practical method to test and improve responsiveness to cyber incidents. It is no coincidence that it has been incorporated into recent Europe-wide regulations (keyword: DORA – threat-led penetration testing). It involves simulated attacks and scenarios that require the collaboration of blue, red, and white teams:
- Blue Team: Defends against and combats attacks on IT applications and networks. These teams typically consist of SOC analysts, SIEM specialists, and CERT members who test their skills and processes in realistic scenarios.
- Red Team: Conducts targeted attacks on target systems to identify vulnerabilities. This team usually consists of internal or external penetration testers and security experts who take on the role of an attacker with the goal of uncovering weaknesses.
- White Team: Gibt Anweisungen, überwacht und bewertet die Übungsszenarien. Das weiße Team besteht aus Moderatoren und Schiedsrichtern. Sie sind dafür verantwortlich objektive Analysen und Feedback zu geben, um sicherzustellen, dass die Übung so realitätsnah und effektiv wie möglich ist.
The overall war-gaming process can be divided into the following phases:
- Planning: Preparation of the exercise scenarios.
- Execution: Conducting simulated attacks by the red team.
- Coordination: Management and alignment of defensive measures by the blue team.
- Implementation: Real-time execution and adjustment of defense strategies.
- Debriefing: Analysis of results to identify opportunities for improvement.
Effective communication and continuous improvement
An essential aspect of war-gaming is not only testing the technical performance of the teams but also their communication skills within the team and with leadership. Especially in the first moments after detecting a new incident, uncertainty often prevails: Is this a targeted attack or just a log file anomaly? Which systems are affected? It is now crucial to keep a cool head and follow the incident response process. This clearly defines responsibilities and provides all participants with confidence in their actions, while the situational picture gradually becomes clearer with each new piece of information.
As the teams’ maturity and experience increase, the requirements can be gradually raised, from predefined exercise scenarios to real attacks tested in simulations. This ensures that your company is optimally prepared for all eventualities.
Conclusion
The incident response process is the structural backbone of effective cyber defense, which can only unfold its impact through the expertise of SOC, SIEM, and CERT. Regular war-gaming exercises continuously put these capabilities to the test and strengthen responsiveness. This way, companies can sustainably enhance their resilience against cyberattacks and remain capable of acting even in times of crisis.




