
No cyber strategy without user access management

In an increasingly digitalized world, where more and more processes, transactions, and data flows are handled online, the need for reliable and secure identity management is steadily growing. This is where User Access Management (UAM) comes into play – a crucial component that forms the backbone of every effective IT security strategy.
What is UAM?
User access management generally refers to the administration, monitoring, and control of user access to various system resources. It essentially operates according to the principle of least privilege and is divided into two main areas:
Identity and Access Management (IAM)
Privileged Access Management (PAM)
Identity and Access Management
The heart of IAM: The IAM area consists of various sub-disciplines, each of which plays a specific role in the overall system:
- Governance and processes: This is where the rules and workflows are defined. This includes, for example, the IAM policy framework, the target operating model, and the reporting model, as well as core processes for handling change requirements (e.g., the joiner-mover-leaver process), to name just a few.
- Business unit tasks: This area deals with the practical implementation of IAM policies in day-to-day business. This includes maintaining authorization concepts, segregation of duties (SoD) such as the four-eyes principle, and the definition of business roles.
- Technology: Technology is the tool used to implement IAM policies. This includes platform development, application integration, the technical onboarding of authorization concepts, and much more.
Only through the interaction of these disciplines can effective identity and access management be ensured—and, above all, tracked.
The specialized focus of PAM: With great power comes great responsibility—and greater risk in the event of intentional or unintentional misuse. While IAM focuses on overall access management, PAM specializes in privileged accounts.
These are accounts with higher access rights than a standard user. Such accounts can be used by humans (e.g., administrators) as well as by machines (technical accounts).
Factors for an effective PAM system
- Protection and management of credentials
- Isolation, monitoring, and recording of sessions
- Threat detection and analysis
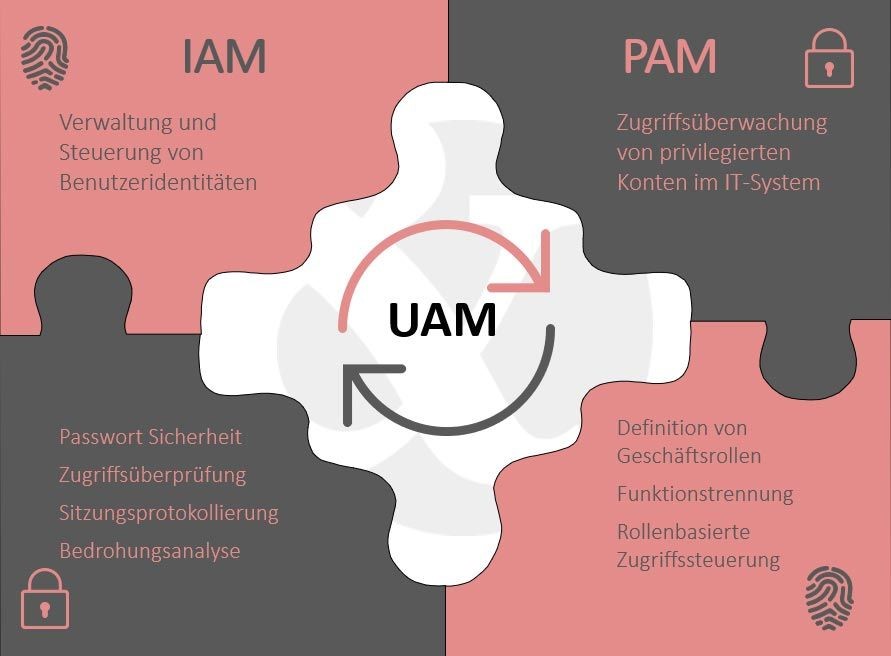
Die Wirkung von IAM und PAM zusammen
The Interaction of IAM and PAM:
The IAM and PAM concepts are two sides of the same coin. While IAM ensures that the right people have access to the right resources, PAM ensures that privileged accesses are secure. Together, they form the basis for effective User Access Management that ensures the integrity, confidentiality, and availability of IT systems within the organization.
At a time when cyber threats are becoming increasingly sophisticated, a solid UAM system is no longer just desirable but essential. On the one hand, it protects the company from external threats, while at the same time ensuring that risks from internal errors or malicious actions are specifically minimized.
There is a wide range of IAM/PAM technologies on the market, and each of these tools offers different functions tailored to specific application areas. In addition to central solutions in the cloud environment, which all relevant players offer in an integrated manner (Azure, AWS IAM, Google, …), there are also numerous providers of specialized software solutions (Sailpoint, Okta, OneLogin, Cyberark, BeyondTrust, Arcon, to name just a few representatives).
As always, it is therefore advisable to carry out a careful software selection process before choosing a specific product and to take into account the individual requirements and needs in order to establish an appropriate IAM or PAM solution.
In a previous post, we addressed the importance of Information Asset Classification, from which, among other things, the protection requirements of one’s own resources and assets are derived. UAM is a core element in achieving these protection requirements. Regardless of which technologies are ultimately used, a well-thought-out and implemented UAM concept is an essential contribution to IT security in every organization.
Horn & Company has extensive project experience in the design, implementation, and operation of functional UAM solutions. Whether at the very beginning or already well advanced, our experts are happy to assist you at every project phase to take your IT security strategy to a new level. If you have any questions on the topic, feel free to contact us.


